Worried about data security in your generative AI projects? Safeguarding sensitive information has become more critical with the increasing use of AI. Your data can be vulnerable to breaches and misuse in the absence of proper security measures. This can lead to significant setbacks, loss of trust, and potential legal issues. It’s like building a house with no walls. Your valuable information is left exposed. But you don’t need to fear as this blog covers nine powerful tips to enhance data security in generative AI. It covers strategies that will help you protect your data and ensure your AI projects are safe and secure. Ready to fortify your data security? Let’s dive in and build a robust defense for your generative AI endeavors!
.webp)
Training generative AI models require high-quality and diverse data. However, finding this high-quality data isn't always straightforward. AI's output can be skewed or inaccurate if the data is biased or incomplete. Ensuring the data is comprehensive and representative is key to building robust and reliable generative models. Consider collecting diverse datasets that represent different scenarios and perspectives accurately.
Training generative AI models requires hefty computational resources. Imagine running multiple high-powered machines simultaneously, crunching numbers, and learning patterns; it’s a resource-intensive process. This massive computational need translates into significant financial costs. High-performance GPUs or TPUs and substantial storage capacity are essential, making the training process not just a tech nical challenge but also a financial one. Balancing these costs with performance needs is crucial for any organization venturing into generative AI.
The main ethical issue with generative AI is that it can embed and spread biases. These biases can affect decisions and outcomes, leading to unfair treatment. Addressing this challenge requires careful monitoring and intervention. By recognizing the biases early, we can take steps to ensure fairness and accuracy. This approach improves AI systems and builds trust in their use.
Must Read: How Generative AI Can Be Used in the Real World?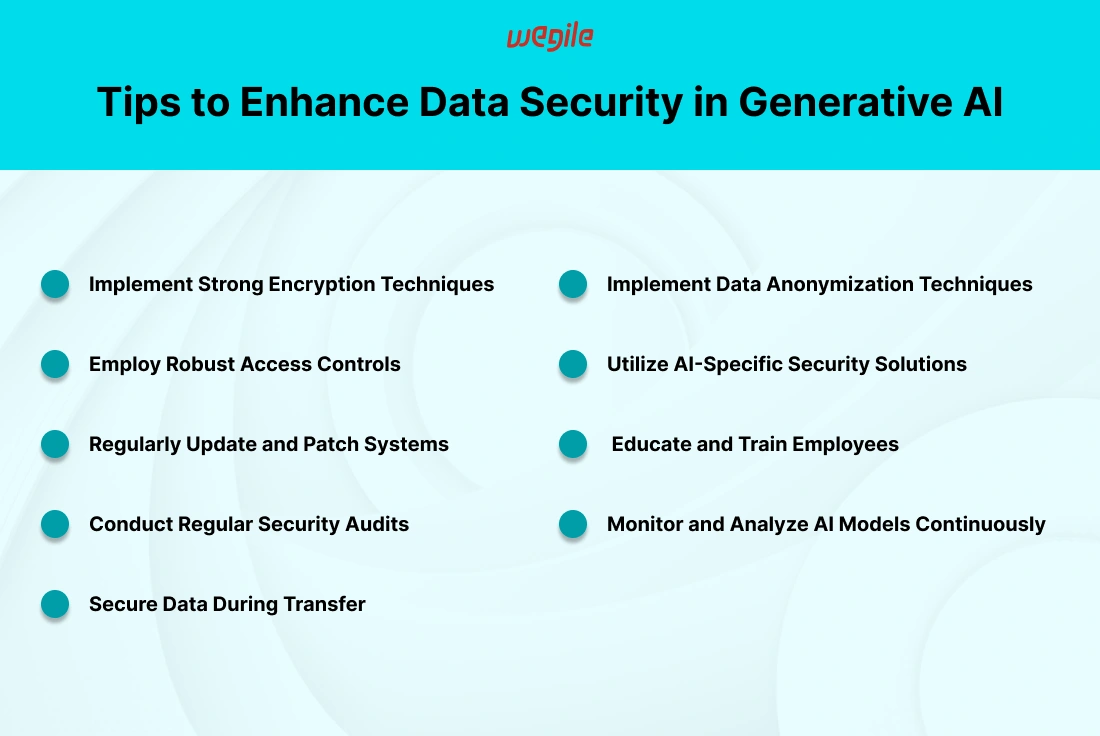
Encryption is crucial to secure AI's data. But how does it happen? There are two main ways that you should consider. 1. Symmetric and 2. Asymmetric encryption. Symmetric encryption requires only one key to encrypt and decrypt data. This makes it a speedy process; however, make sure to handle the key securely. On the other hand, asymmetric encryption uses a pair of keys: one is public, and the other one is private. This adds an extra layer of security but at the cost of additional computational overhead. Both methods are crucial, and choosing the right one depends on your specific needs and data sensitivity.
Always use strong, updated encryption algorithms and manage keys securely. These practices will get you the most out of encryption. Update the encryption protocols regularly to keep up with evolving threats. Additionally, ensure encryption is applied consistently across all data points. This is required both in transit and at rest. Follow these best practices to protect your data against breaches and unwanted access.
RBAC restricts access to sensitive information so that only authorized users may view it. Data access, modification, and view permissions can be better managed with it as it allocates roles and permissions according to job functions. This guarantees only those who need sensitive information can find it and also reduces the risk of unauthorized access.
MFA enhances security by prompting users to confirm their identity through multiple methods. Think of it as having a double lock on your front door. When one key is compromised, you can rest assured that the second layer is ready to keep the entry secure. You can ensure that access is closely monitored and greatly minimize the chances of unauthorized entry by incorporating MFA into your generative AI environment. Rest assured, knowing that your data is fully protected and secure.
Consider regular updates as the necessary maintenance for your AI systems. They safeguard your system from potential vulnerabilities. Keeping your systems updated is crucial for staying ahead of any risks. Software developers are always working hard to find and fix security issues. Not keeping up with updates is like forgetting to lock your door. You’re surely going to invite trouble. Thus, it's important to regularly update your systems so that they can effectively handle any new security threats and operate at their best.
Manual patching can be tedious, but automated solutions make it a breeze. Automated patch management tools handle updates for you. It ensures that your systems are always up-to-date without constant manual intervention. These tools monitor for vulnerabilities and apply patches automatically. This saves you time and reduces the risk of missed updates. Embracing automation means you’re not just staying current but staying ahead.
Security audits are like regular check-ups for your AI systems. Identifying difficulties in advance prevents them from escalating into significant problems. Various types of audits exist, each fulfilling a distinct function in the identification and mitigation of potential hazards. This ensures your AI systems remain robust and secure.
Internal Audits: These inspections are carried out within your organization. Internal audits provide a glimpse into your security posture from an insider's point of view.
External Audits: These inspections are carried out by independent professionals. Getting an external audit can give you a fresh perspective on your security practices and help uncover any blind spots that may have been overlooked.
Finding issues in an audit is just the beginning. The real work begins with acting on those findings. Prioritize the audit recommendations first by taking into account their impact and risk. Make a comprehensive strategy that takes into account all of the issues, identifies who will do what, and sets due dates. Maintaining a high level of data security requires periodically reviewing and revising security rules in response to audit results. You can strengthen your defensive measures and fix any holes in them by taking proactive actions.
It's important to make certain that data remains secure and intact during transfer calls. This requires reliable and strong methods to prevent any unauthorized interception or tampering. For a more laid-back and technical approach, you can rely on secure transfer protocols such as HTTPS, FTPS, and VPNs. Employing these methods guarantees the security and integrity of your data while it is being transferred.
HTTPS: It encrypts data between your browser and the server. This makes HTTPS essential to secure web interactions.
FTPS: It offers a secure way to transfer files and adds encryption to the standard FTP.
VPN: It creates a private network over the internet and protects your data from prying eyes.
Data integrity checks are the security guards for your data that make certain that it arrives unchanged. These checks verify that the data sent matches the data received, and they further flag any alterations. Checksums and hash functions employ methods to produce distinct identifiers for data and enable comparison before and after transmission. If the identifiers match, you know the data is intact. Implementing these checks adds an extra layer of security. This ensures that your data remains unaltered and trustworthy.
Anonymizing data deals with protecting identities while retaining useful information. There are methods to ensure that even personal information remains protected even if data is accessed without authorization. Several techniques can achieve this:
Data Masking: The approach replaces sensitive data with random but realistic values. This makes it unreadable to unauthorized users.
Tokenization: This approach substitutes sensitive data with unique identifiers (tokens) that retain the original data’s usability but conceal its true form.
Data anonymization poses a problem in balancing privacy concerns with its practicality. Ensuring user identity protection without sacrificing the data's usefulness is like walking a tightrope. Data analysis becomes impossible when it is over-anonymized. Also, it becomes risky when it is under-anonymized. Thus, you need to strike the right balance here, which involves understanding the specific use case and applying the appropriate level of anonymization. This careful calibration makes certain that data remains both secure and functional for its intended purposes.
AI-driven security tools are like having a digital watchdog that never sleeps. These advanced tools use machine learning to detect and respond to threats in real-time. They can identify unusual patterns, flag potential security breaches, and even automate responses to contain threats. Thus AI-driven tools, by continuously learning from new data, become more effective over time and provide a robust defense against evolving cyber threats.
The development of AI should incorporate security measures. You can't just throw it on as an afterthought. Putting security first from the very beginning of the design process is where it all begins. Further, approaches such as secure coding practices, conducting regular code reviews, and implementing thorough testing enable the early detection of vulnerabilities. Also, the incorporation of automated security tools into the development pipeline will result in identifying and fixing issues before deployment. This proactive approach ensures that security is an integral part of your AI solutions and guarantees protection from the ground up.
Having a knowledgeable team is crucial for protecting against security threats. It's important for security training programs to cover key topics such as identifying phishing attempts, practicing safe data handling, and emphasizing the significance of regular software updates. Practical workshops and realistic simulations can boost learning and improve long-term memory. Also, providing employees with the necessary training and knowledge can significantly reduce the chances of human error compromising your data security.
Building a security-first culture means ensuring everyone takes responsibility for it. Therefore, open communication about security issues is important. Additionally, recognize and appreciate employees who proactively safeguard data. To maintain vigilance, keep the team informed about new threats and the steps to handle them. Moreover, it encourages good security practices by implementing rewards or recognition programs. Ultimately, when security becomes a core value shared by the whole organization, it strengthens your defense strategy and helps maintain robust data protection.
Think of continuous monitoring as having a security camera installed to keep watch over your AI models. It ensures they stay on the right track. There are several tools and techniques you can use to monitor effectively:
Logging and Alerts: Set up comprehensive logging to track model behavior and alarm systems to keep you informed of any unusual occurrences.
Performance Metrics: Regularly measure key performance indicators (KPIs) to identify any deviations that could indicate potential security issues.
AI-Specific Monitoring Tools: Employ specialized tools designed to monitor AI models. These tools provide customized insights into the performance and security of the models.
Swift and effective response is crucial in the times when a security incident occurs. Here’s a framework to guide your actions:
Incident Identification: Quickly identify and confirm the security breach using your monitoring tools.
Containment: Stop the breach in the initial stages and stop it from spreading by isolating the compromised systems right away.
Eradication: Identify the root cause of the incident and eliminate it from your systems.
Recovery: Restore affected systems and verify that they are functioning correctly and securely.
Post-Incident Analysis: Conduct a thorough review of the incident to understand what happened and how to avoid repeating the same mistakes in the future. Update your security measures and protocols based on these insights.
Now that you have explored the crucial nine tips, you should be able to secure your generative AI projects' data much better. Putting these ideas into practice will secure your sensitive information and establish trust with users to prevent future problems. Embrace these security measures to ensure your AI projects remain robust and secure. Ready to take your generative AI security to the next level? Wegile’s generative AI development services can help you build and secure your AI solutions with expert guidance. Let us help you uild robust AI projects that stand out. Reach out to Wegile today, and let’s secure your AI future together!
 Browse Our Services
Browse Our Services
